The Blockchain Bet: How Decentralized Tech is Reshuffling the Deck for Mobile Gambling
High-tech is going through a Renaissance nowadays. For those blissfully unaware, the changes in familiar spheres of life can be dramatic, but they’re all for the best. Ever tried explaining blockchain to your tech-averse uncle? Yeah, real head-scratcher. But believe it or not, because that same technology, blockchain, is quietly transforming the world of online […]
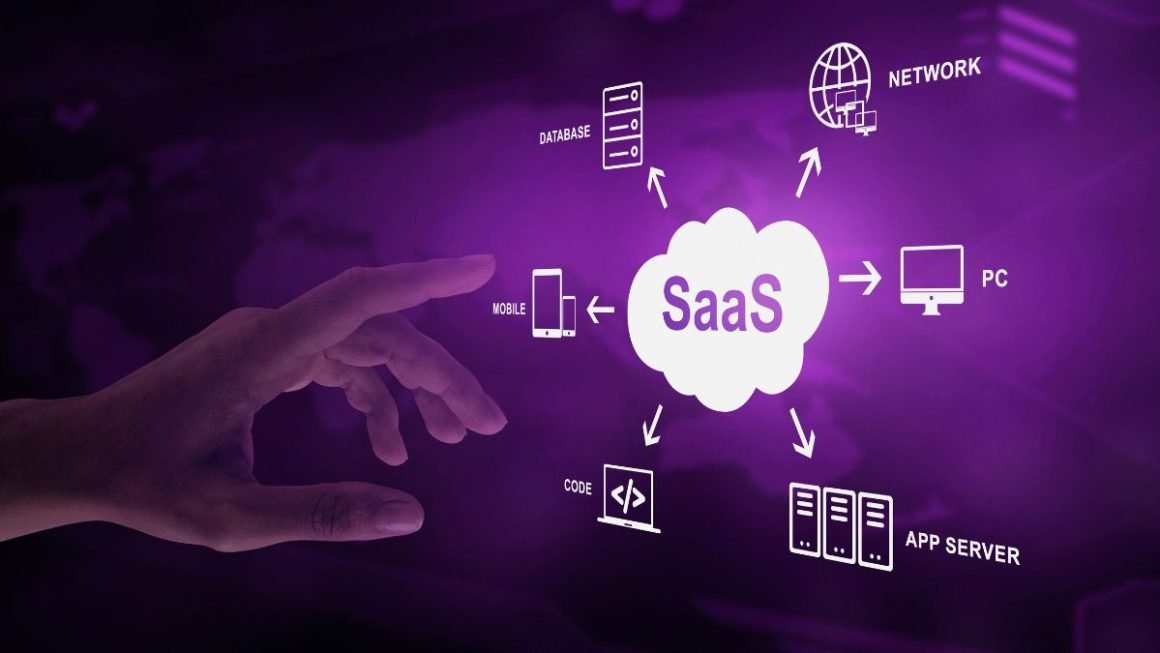
SaaS Application Development And The Art Of User Experience Design
The SaaS market is quite competitive these days, which makes it quite a challenge to develop new software-as-a-service applications. One of the components of any online service’s success is the way it looks, specifically the way users interact with it. Ladies and gentlemen, in this article we are going to talk about creating an engaging […]
Everything You Should Know About Oracle HCM 24A Release
There is no doubt that Oracle is committed to continuous innovation. They release quarterly updates across various modules, such as HCM, financials, and SCM. In the HCM module, the Oracle HCM 24A release brings several features and enhancements to empower HR professionals, streamline various processes, and improve overall employee experience. Let’s delve into the specifics […]
What Microsoft Office 365 For Business Includes
Surely, we have all, at some point, used Word, Excel, or PowerPoint. The reason is that these programs have been with us since 1989 when the North American company Microsoft launched its first official version of Office for Mac and the following year for Windows. Then, for more than thirty years, numerous updates have been […]
Traditional WAN vs SD WAN What It Is And What Differences There Are
Traditional WAN and SD-WAN are two terms that are becoming increasingly popular in the technology world. And with the ever-increasing demand for bandwidth, many companies are looking for an alternative to the “old-fashioned” WAN. But what is each of them? What are the differences? In this article, we will clarify doubts about these two solutions […]
Maximizing Efficiency In File Data Management With PDF Editors
In today’s digital age, efficient file data management is essential for businesses and individuals alike. As the volume of digital documents continues to grow, the need for effective tools to organize, extract, and collaborate on data within these documents becomes increasingly important. PDF editors play a crucial role in this process, offering a wide range […]
Logistics And Legacy: Training In Application Development And The Reconstruction Era’s Impact On Education
We shall examine the long-lasting effects of the Reconstruction Era on education in this extensive study paper, with an emphasis on how this crucial historical era influenced contemporary application development training. To give students a plethora of tools for efficient research and writing, we will walk through this important relationship while introducing you to a […]
Factors To Take Into Account When Purchasing A Server
Digitalization is the key to the survival of companies in the 21st century, and servers help take that step towards digitalization. Today, servers have become a key tool for transforming business operational processes. Its improved efficiency and reduced costs have democratized access to this type of technological infrastructure by companies. Despite this, many projects still […]
How Do I Know What My IP Is According To My Operating System?
To find out your IP, you must navigate to the Wi-Fi or Ethernet settings regardless of the device and software you are running. This is how you should do it, depending on the operating system you use: Find out IP in Windows from your PC: On the taskbar, select Wi-Fi or Ethernet > Click on […]
What You Need To Know About the Best Free VPN With Unlimited Data
A free VPN is a fantastic choice for anyone wanting unlimited data and internet access. Internet without cost. Although it’s important to note that the VPN isn’t a free Internet, it can improve your browsing experience by removing limits on data usage and providing security. However, completely free VPNs could have limitations like limits on […]